To remain competitive, modern technology businesses should take steps to implement responsible business practices that customers, employees and partners expect.
Customers want to purchase products that protect the environment and improve local communities. A useful tool to pursue inclusive growth is a sustainability balanced scorecard.
Below is an example sustainability strategy map I developed for a technology startup.
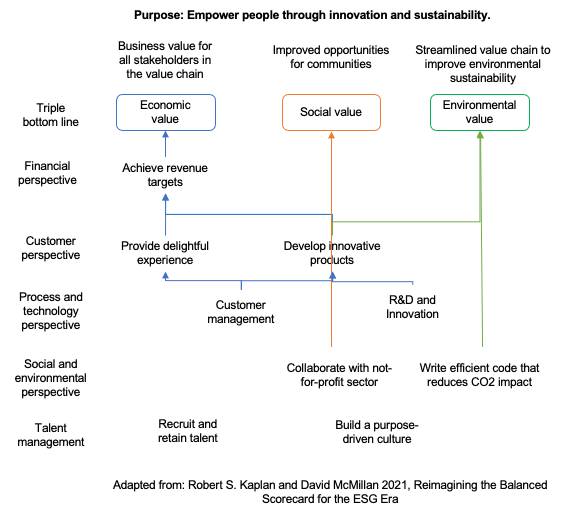
For a technology business, environmental impact can be achieved through close examination and streamlining of company’s supply chain, including datacentres and cloud infrastructure providers. Companies could also analyse their software development lifecycles to make it more sustainable.
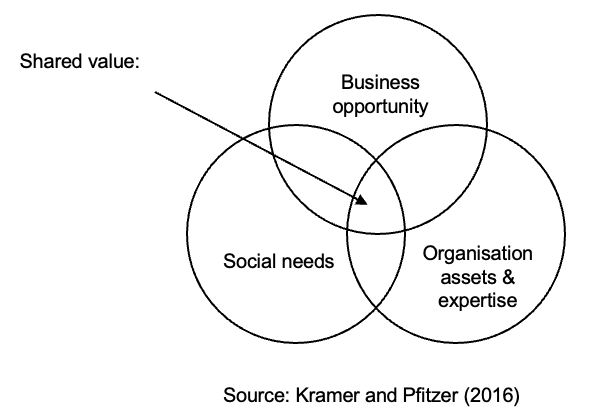
Achieving financial objectives can produce societal benefits through creating shared value.
Finally, implementing responsible business practices aligns with UN Sustainable Development Goals (SDGs), specifically SDG9: Industry, Innovation and Infrastructure and SDG17: Partnerships for the Goals.