
Following-up on my recent update on starting an Executive MBA, I wanted to share that I’ve reached a milestone in my learning journey; I’m half-way through with six modules completed.
I already wrote about Data Analytics and Decision Making and in this blog I’ll briefly summarise a few other courses I’ve completed and how some of the learnings can be applied to cyber security leadership.
Leadership
Leadership is the foundation for creating a supportive and inclusive work environment. It is a compulsory starter course aimed at deepening the knowledge and applying leadership concepts to real-world situations. It had an intensive face-to-face component that enabled me to practice various leadership techniques in a group setting. The peer and facilitator feedback were particularly useful in developing the new skills.
Responsible and ethical leadership were a big focus of the course and resonated strongly with me as they have direct applications to cyber security leadership and crisis management.
Some of the frameworks could be applied directly to the workplace challenges. For example, one can leverage the DACA model (Direction, Alignment, Commitment and Ability) to do an ‘environment scan’ and understand the context of an organisation. It can reveal areas of improvement: there may be no clear mission or goals, lack of engagement and clarity on roles due to multiple recent reorganisations, constant ‘firefighting’ while struggling to plan and resource important work. Setting a clear direction therefore is a priority. And it’s important for this direction to be grounded in values.
Synthesising and applying these learnings has made me a more adaptive leader who can solve complex cyber security and business problems.
Marketing Management
This was one of the most eye-opening courses for me personally. The range of marketing frameworks taught was very useful to get an understanding of customer behaviours. This allowed me to develop skills to build compelling value propositions. I had a chance to apply marketing concepts in practice through the analysis of various case studies on Amazon, Nike and other organisations. These ranged from brand activism to merging digital and physical worlds for market growth.
Marketing models like AIDA (Awareness, Interest, Desire, Action) have direct application in cyber security communication, particularly security awareness campaigns, security culture and behaviour change efforts.
Brand and Product concepts and frameworks, particularly the brand resonance pyramid (Keller 2020) and the growth vector matrix (Ansoff 1957) can be applied in cyber security too. For example, consider last year’s Optus (Australia’s second largest telecommunications company) breach. I put the below diagram together to demonstrate how this framework can be used to evaluate the impact on Optus’ brand.
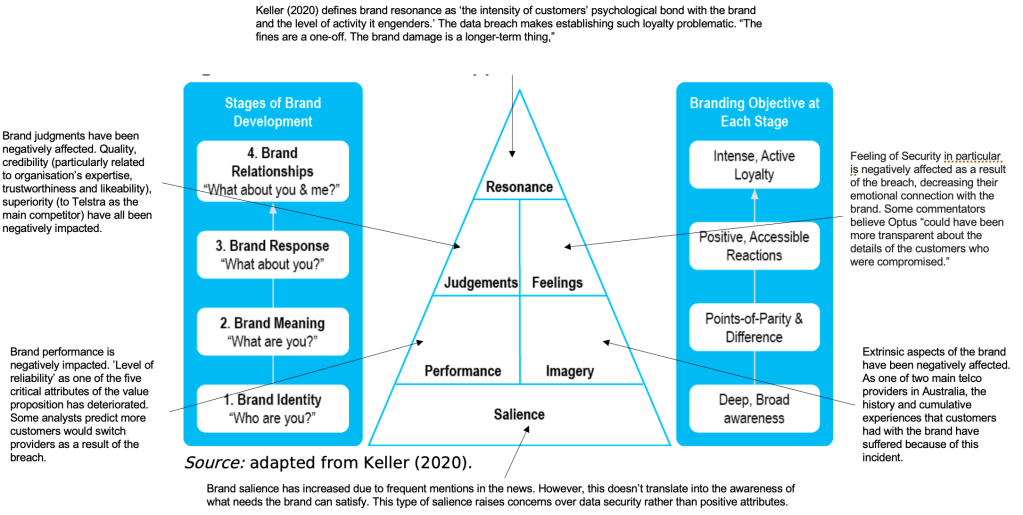
Finally, engaging in the the marketing management simulation was a great way to apply course concepts and frameworks in a real-world scenario. It this group assignment we leveraged insights derived from marketing information system to guide our marketing and pricing decisions and deliver customer value.

Careful market research and investment in understanding the needs of our target segment allowed us to implement product enhancements that resonated with our customers. Segmentation, targeting, differentiation and positioning efforts allowed us to successfully position the company in the minds of customers as a high-quality differentiated gravity brand for our prime customers.
Accounting and Financial Management
This course was certainly outside of my comfort zone, however, it’s definitely one of those core ones that every MBA student is encouraged to take. I’m glad I did as I’m now much more comfortable interpreting financial statements and analysing a company’s financial performance. Accounting and finance is also the language business executives and Boards speak, so it’s useful to have a common ground and be able to align security initiatives to wider business objectives.
While working on assignments and preparing for the final exam, I learned how to analyse ratios like return on equity, profit margin and asset turnover. This provided insight into companies financial position and operating performance. Other important topics included product and service costing, profit and liquidity planning, capital investment analysis and budgetary control.
I feel much more confident preparing and managing security budgets, analysing capital investment decisions and assessing return on investment for security projects using tools like net present value and internal rate of return.
Strategy
Strategy was my favourite course so far! I really appreciated the interplay between the ‘traditional’ frameworks for strategy covered in earlier units and the ones focused on innovation. Being able to see how these complement (rather than contradict) each other will allow me to apply a more holistic approach to strategy development and implementation in my current and future roles. I also learnt how these frameworks work together. I particularly liked the synergy between the Industry Value Chain and Porter’s Five Forces, where each link of the value chain can contain its own five forces analysis. This can be useful for framing the context and also visualising where profit is being made in the value chain.
The layout of the course helped me break down the otherwise complex simultaneous process of analysis, formulation and implementation into manageable chunks. I particularly liked the last unit that brought it all together and helped me further conceptualise the course models and frameworks and apply them in practice in my cyber security role. I can now develop richer cyber strategies that are grounded in research and the latest academic developments.
One of the most important insights for me was the realisation that the tools and frameworks that I covered in this course are a means to an end, not an end in themselves. Strategy development in the real world is complex and these frameworks, while helping make sense of complexity, don’t reflect reality perfectly and don’t always fit. They are, however, useful in stretching our mental models. People can have different points of view on their application that are equally valid. Personal opinions have biases though, so thorough research and evidence-based reasoning are important to have credibility.
Finally, having guest speakers share their stories was another highlight. It was so insightful to see how some of the course concepts were applied in the real world and made the whole experience much more practical.
I’ve also had a chance to do an international exchange for the fall semester at Yale School of Management. I’ll summarised my learning from this course in a separate blog.
I look forward to the next year!
7 Comments