Scenario analysis is a powerful tool to enhance strategic thinking and strategic responses. It aims to examine how our environment might play out in the future and can help organisations ask the right questions, reduce biases and prepare for the unexpected.
What are scenarios? Simply put, these are short explanatory stories with an attention- grabbing and easy-to-remember title. They define plausible futures and often based on trends and uncertainties.
This approach was pioneered by Shell (disclosure: I was a cyber security consultant at Shell) to anticipate multiple likely futures to reduce uncertainty and start framing a potential strategic direction. You can read more about Shell’s approach on their website, I recommend the Sky scenario in particular as it relates to sustainability and energy transition. This 4-minute video is a good introduction; for a deeper dive, I recommend this 15-minute video overview.
Generative AI, with appropriate prompting can be very useful in generating some of these scenarios.
Ultimately, the point is not to just have a collection of scenarios but rather to do something with the insights derived from them. For example, scenarios are often used as a driver to build in resiliency or put systems in place to monitor for likely changes so they can take quick action and adapt.
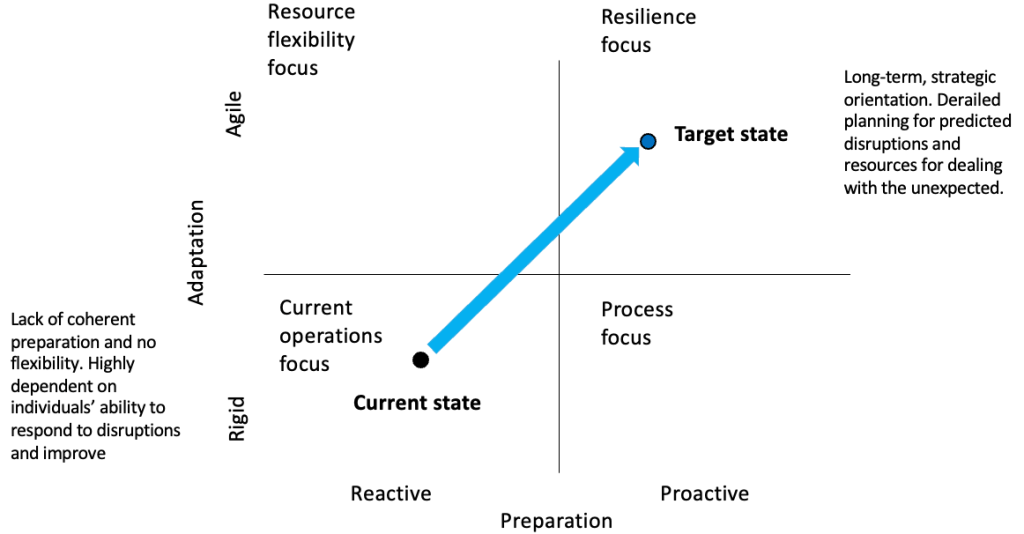
The resilience matrix is a useful tool that can be used to complement scenario analysis and help organisations become more future-proof. It can be leveraged to assess the degree to which organisations focus on adaptation version preparation.
To get to the target state of organisational resilience, I recommend focusing on seven key elements (defined by Gartner consultants):
| Element | Actions to build resiliency |
| Leadership culture | Ensure company values promote resilience and adaptability |
| Workforce | Train people to navigate uncertainty and change effectively |
| Systems and processes | Develop and regularly update business continuity and disaster recovery plans for critical functions |
| Facilities | Implement protocols to ensure workplace safety during emergencies |
| IT | Establish robust backup and recovery systems for critical data |
| Cybersecurity | Develop and test plans to respond to cybersecurity incidents swiftly |
| Supply chain | Evaluate and mitigate risks within the supply chain through regular assessments |
In the cases where sustained action is not possible, we can use scenarios to develop an early warning system to constantly monitor for weak signals as shown in a simplified example below.
| Type of signal | Source of signal | Signal gathering method | Trigger to take action |
| Technological advancements | Tech blogs and industry conferences | Monitoring industry publications and events | Significant increase in in-scope technology adoption |
| Regulatory change | Government policy announcements | Regulatory updates and industry forums | Introduction of new regulatory standards |
| Shift in customer preferences | Market research, cultural trends | Customer feedback, trend analysis, case studies | Demand for in-scope products and services |
In the cyber security context, we can use scenario analysis to manage risks and develop mitigation strategies.
They can take a form of a post-mortem cyber incident analysis framed as a pre-mortem. Such analysis describes potential impact, including financial loss, reputational damage as well as recovery costs. The key is to clearly outline steps required in response to the scenario unfolding as well as in advance to prepare improved mitigations.
CISA released their Secure Tomorrow series focusing on evolving risks that could significantly affect the critical infrastructure in the next decades. It aims to help explore the impact of emerging technologies and disruptive trends and contains a collection of excellent scenarios to explore.
These materials can be used for scenario analysis workshops to shape the broader cyber security strategy and prepare the organisation to respond to the worst case by pre-planning what triggers to look for. They are also an excellent Board and business stakeholder communication tool that can help illustrate strengths and potential weaknesses, and justify the need for cybersecurity investment.