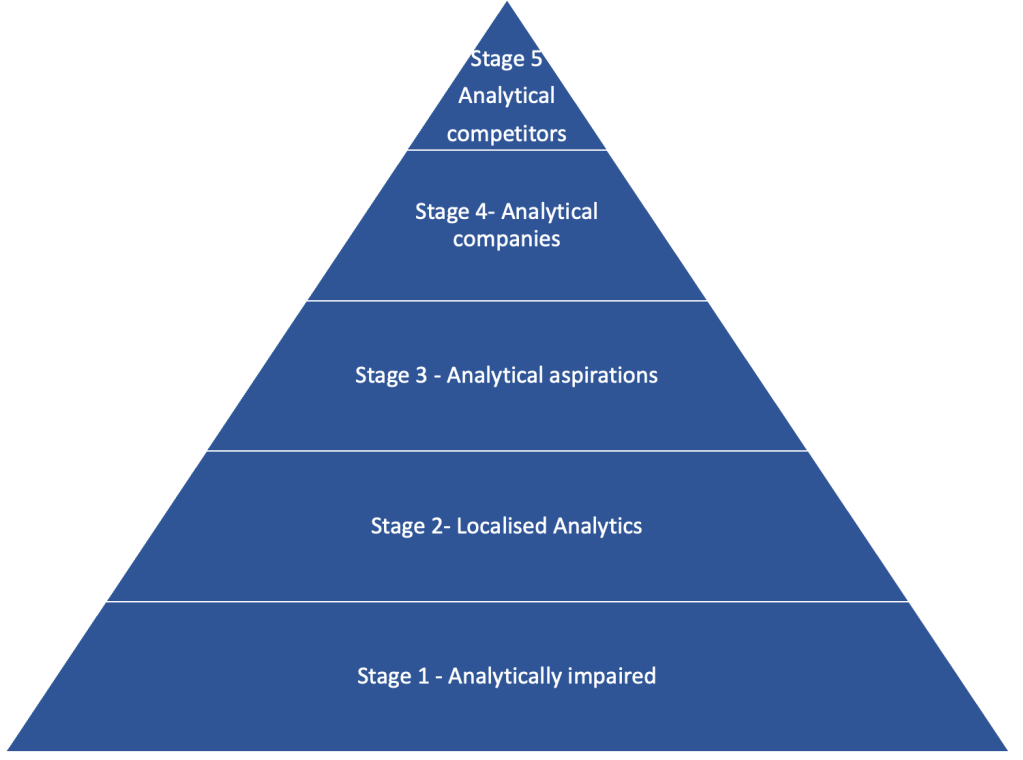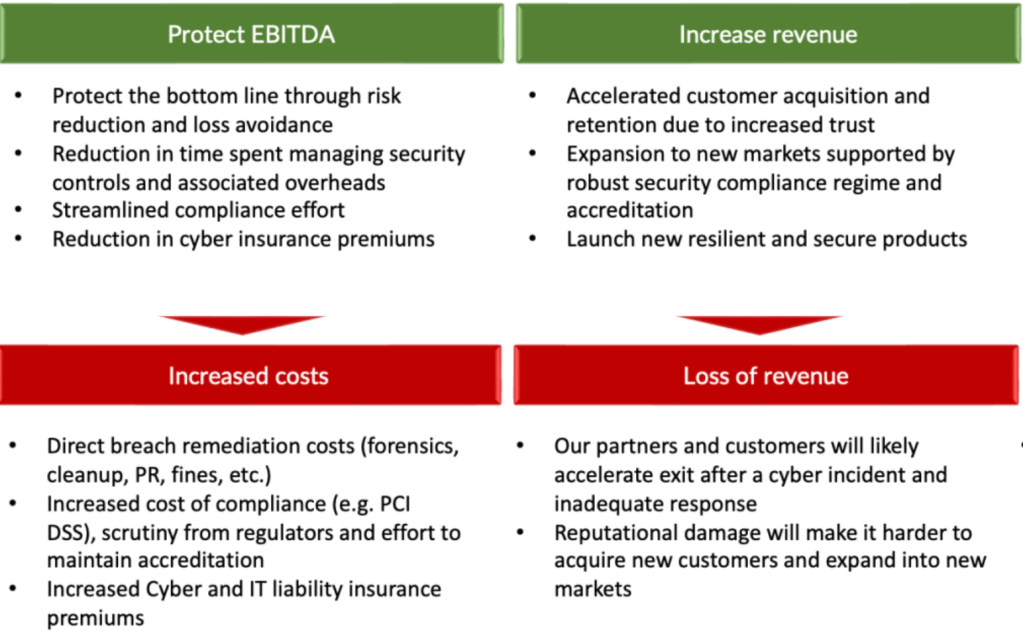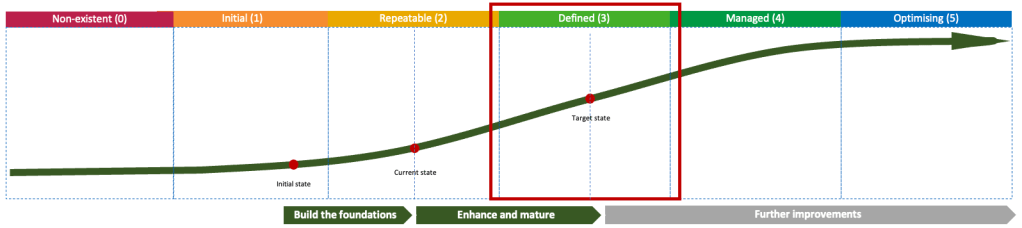
CISOs and security leaders are often called upon to develop a security strategy. It’s an important step to understand what your current state is, in what direction you’re going and the roadmap to get there. It’s also an opportunity to demonstrate how cyber security activities and programs align to business objectives.
There is more to the CISO role than just setting the direction, however. It’s also about execution. As a security leader, it’s key to take ownership of the strategy and deliver on its promise. It’s useful, therefore, to be able to track progress against your objectives and demonstrate to the executive leadership team and the Board the impact the security team is making in enabling the business.