I just spent an incredible week immersed in Aboriginal culture, where I had the privilege of working shoulder to shoulder with First Nations organisations as part of my AGSM Executive MBA journey.
This experiential learning project allowed me to take the academic knowledge from all my previous MBA courses and apply it in real-world contexts. What a great way to wrap up the program!
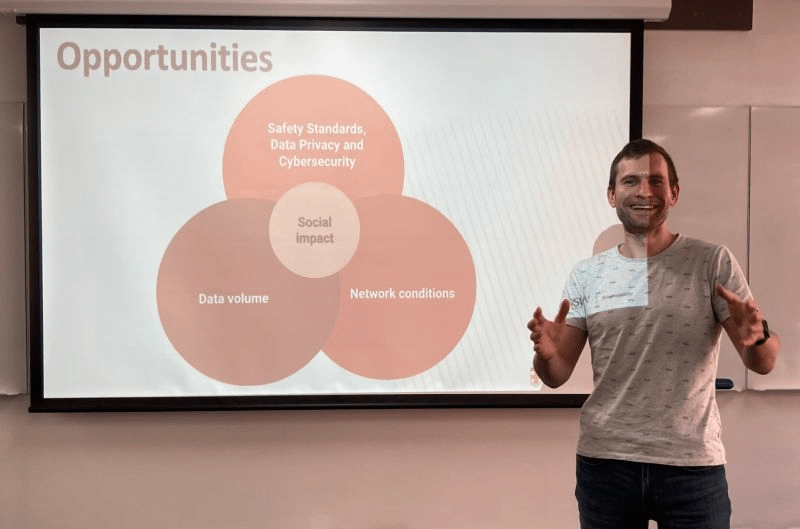
It was also an opportunity to deliver the final client presentation to Indigiearth, a 100% Aboriginal-owned native foods business, concluding the capstone strategic consulting engagement we’ve been working on this term.
Learning directly from Elders and community members enriched my understanding of Aboriginal traditions, values and the profound connection to land that underpins Indigenous enterprises. I’m proud to have been a part of this journey, bringing together cultural respect and strategic vision.