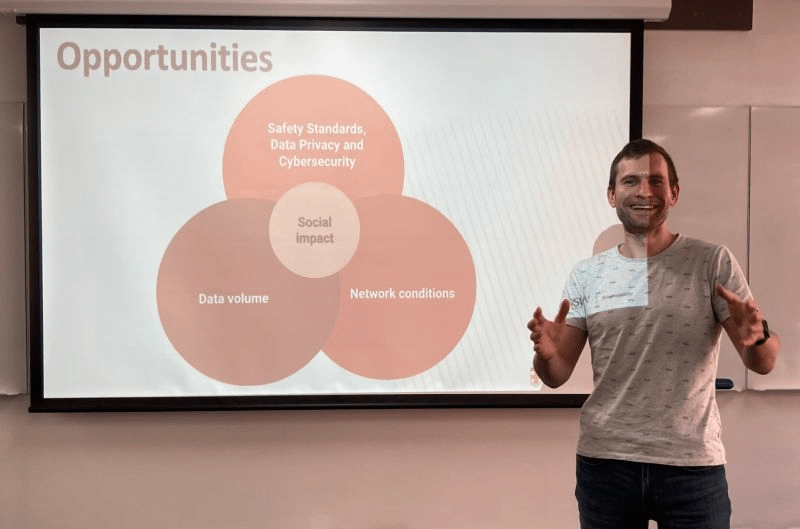
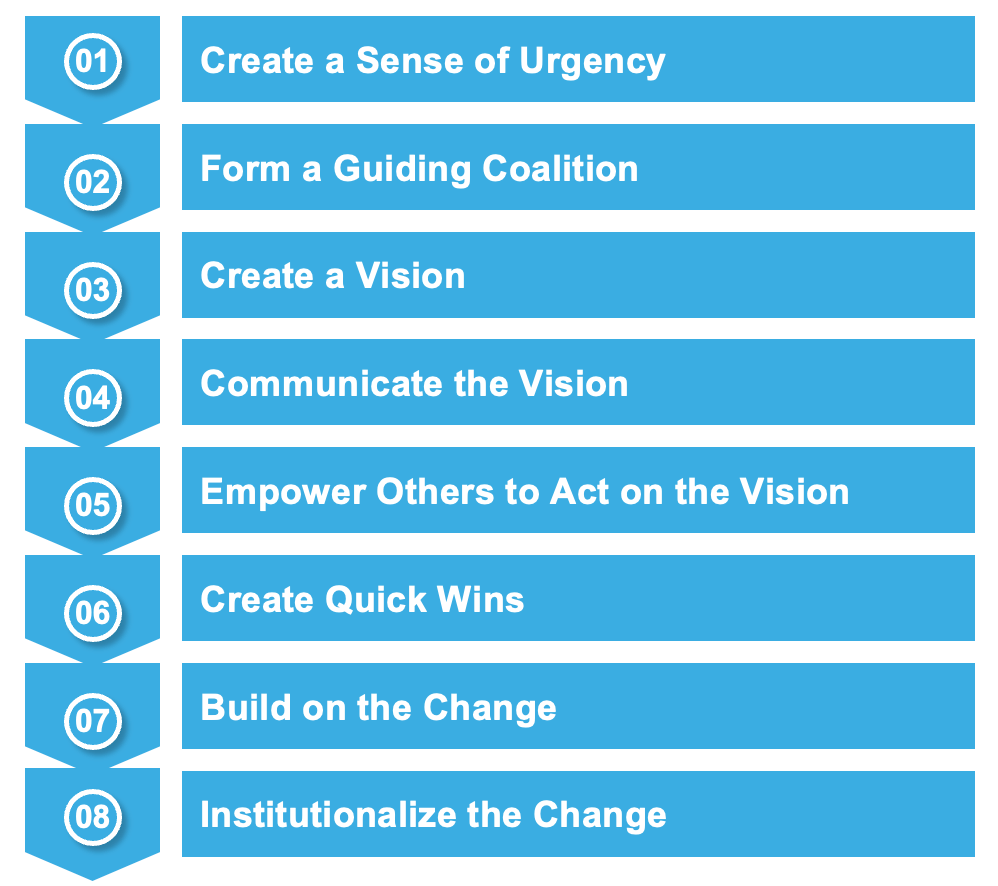
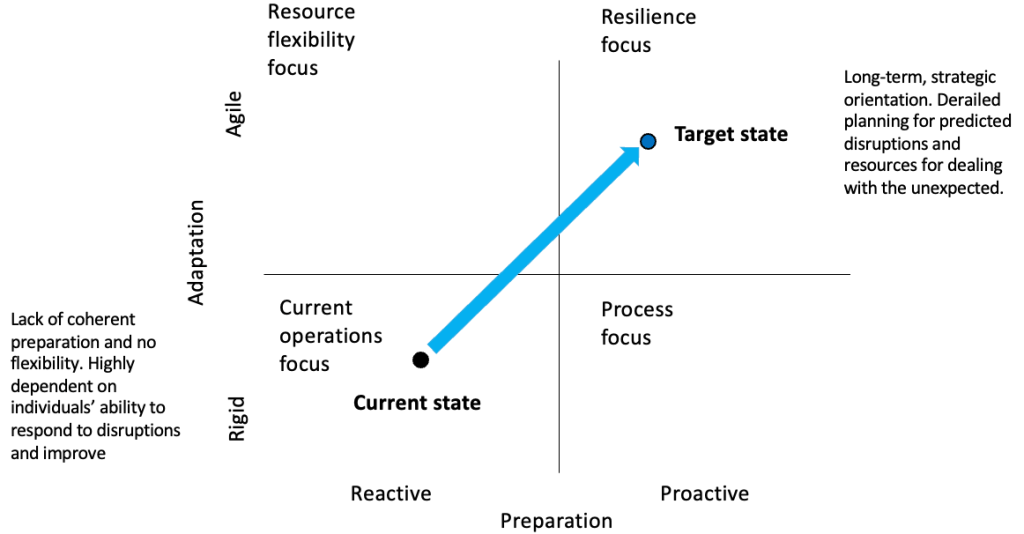
In cybersecurity, collaboration is essential. With growing complexity in the threat landscape, leaders often find themselves working with parties they may not fully align with—whether internal teams, external stakeholders, or even rival firms.
Adam Kahane’s book Collaborating with the Enemy: How to Work with People You Don’t Agree with or Like or Trust outlines principles for collaborating effectively, especially in challenging environments where trust and agreement are minimal. Kahane’s “stretch collaboration” approach can transform the way cybersecurity leaders address conflicts and turn rivals into partners to meet critical security goals. In this blog, I’ll share my key takeaways.