It’s been fantastic to have an opportunity to give back to the community and volunteer with ISACA this year.
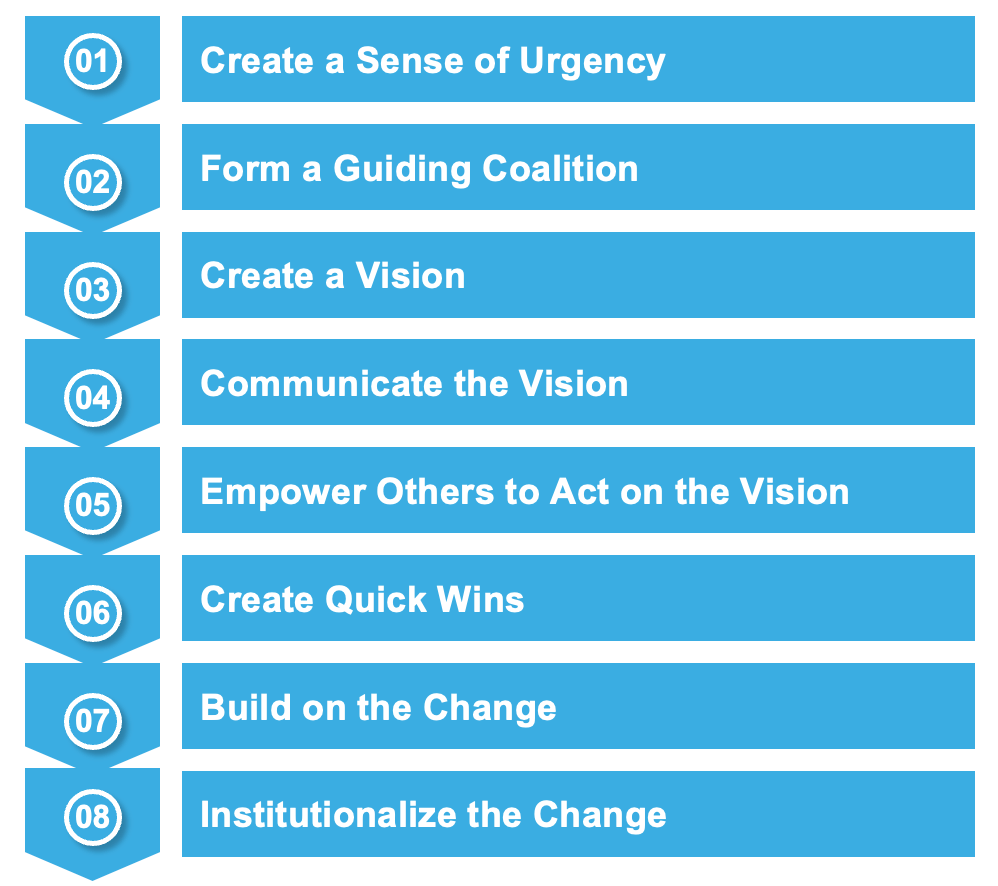
The Sydney Chapter hosted a number of professional development events for cyber, risk, governance and IT professionals with a common objective of building digital trust and securing our interconnected world. I had a chance to support these initiatives, ranging from fundraising for a mental health charity to helping organise conferences.
I found this experience incredibly rewarding and made some good friends along the way.