Many business have felt the economic impact of the Covid pandemic. Depending on the industry, some managed to adapt and pivot to new models and ways of working, but not all were successful.
As a result, some companies were unable to continue to operate profitably and entered administration. The cause of financial troubles, however, doesn’t have to be pandemic-related to pose new security challenges.
In this blog I would like to share some of the priority areas for a security leader in a business in, sometimes rapid, decline.
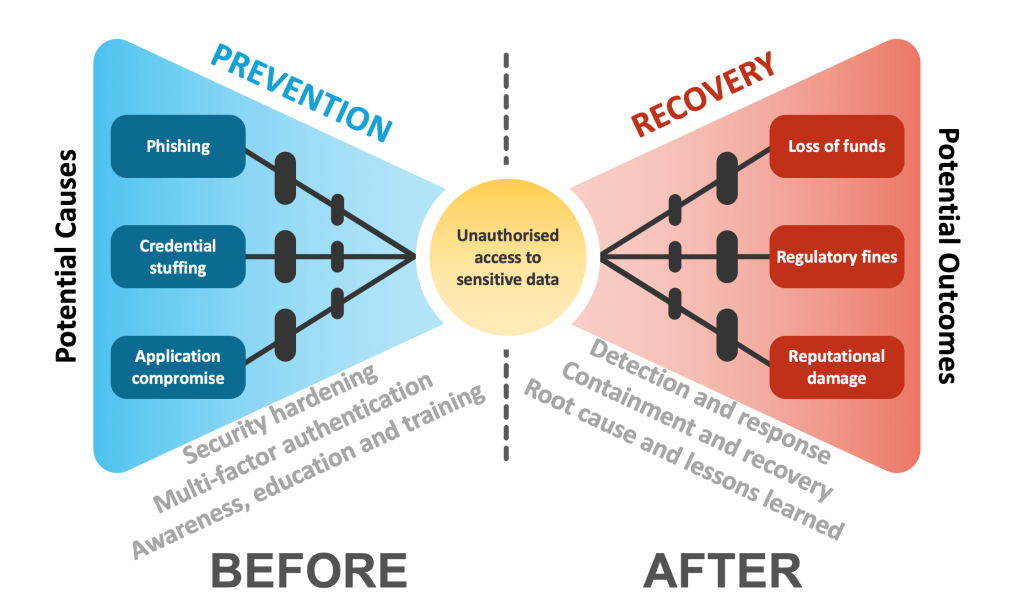
As the business is failing, the leadership might not treat cyber security as their top priority. However, the organisation still has obligations to its customers who entrusted the company with their data and comply with relevant laws and regulations. It goes without saying that previously identified cyber security threats and risks are unlikely to disappear either.
If there is a chance of survival, a poorly managed security incident can be the last straw.
How should security teams adapt? What should they focus on?
Broadly speaking, there are two main areas a CISO can support the business: securing a potential rescue deal and managing the decline.
There are investors specialising in distressed businesses and part of the administration process might involve looking for a capital injection or an acquisition of a failing company.
Potential investors would understandably need to know what they might be buying which normally involves conducting due diligence on the target. Although circumstances are different, the process itself is very similar to an M&A scenario or a startup acquisition.
As a security leader, it’s your job to provide transparency on the matters related to data protection, past breaches and existing security controls and processes. If done right, it presents the business in a favourable light as a well-governed enterprise, increasing investors’ confidence and therefore chances of a successful rescue deal.
In many ways, this is comparable to overseeing a divestment. A lot of such conversations are confidential, so raising awareness of what can and can’t be shared externally (including on social media), and maintaining appropriate need-to-know access controls is paramount.
Some things, however, are outside of our control and sometimes all we can do is to make the best out of a bad situation.
There are a few key areas to pay attention to when it comes to embedding security for a business in downturn.
People. There will naturally be a lot of leavers, so having a robust joiner-mover-leaver process is key. All access permissions should be timely revoked when no longer required. In addition, data loss prevention controls and broader insider risks should be considered as the morale in the company worsens. On a positive note, people and a culture of security can significantly contribute to the company’s security posture, especially in the conditions of scarce resources (see next point).
Resources. Investment in security is going to understandably diminish. Some of the top talent will leave, so you will have to learn to do more with less. If your desired control to mitigate a particular risk is no longer affordable, what is the next best thing? Can this be done cheaper, or better still, for free? Business leadership should be made aware of the potential consequences of risk acceptances, and there will likely be a higher than usual number of these.
Data. There also might not be enough money to pay for non business critical systems and services. These should be decommissioned in the way that ensures that sensitive (including personal) data is destroyed securely in line with company’s retention policies. Having data maps and asset inventories is invaluable to maintain visibility.
Sustaining operational resilience in the face of cost pressure is challenging but not impossible. For many, it’s a unique learning experience regardless of the outcome.