Thank you to everyone who stopped by the book signing. It was a pleasure to meet readers and hear your thoughts. If you missed it, you can still get the book on Amazon:
https://a.co/d/0fai5zyh
A practical approach

Thank you to everyone who stopped by the book signing. It was a pleasure to meet readers and hear your thoughts. If you missed it, you can still get the book on Amazon:
https://a.co/d/0fai5zyh

I had the privilege of joining a panel discussion on the rapidly evolving regulatory landscape and its impact on businesses worldwide. With cyber threats, operational disruptions, and AI risks on the rise, governments are strengthening regulations to drive security, resilience and accountability across industries.
In Europe, major frameworks like DORA (Digital Operational Resilience Act), NIS2 (Network and Information Security Directive) and the EU AI Act are reshaping how organisations approach cybersecurity, operational resilience, and responsible AI governance. But this shift isn’t limited to the EU – regulatory scrutiny is increasing globally, from the U.S. to APAC, with frameworks reinforcing risk management, third-party oversight and AI transparency.
A huge thank you to my fellow panelists and engaged audience members for an insightful discussion.

Cyber security strategy and execution is one of the top priorities for a CISO. It helps articulate the value of security, provide clarity on short and long term goals and outline a cyber security uplift roadmap.
In this blog I recommend a proven step-by-step guide for developing a cyber strategy.
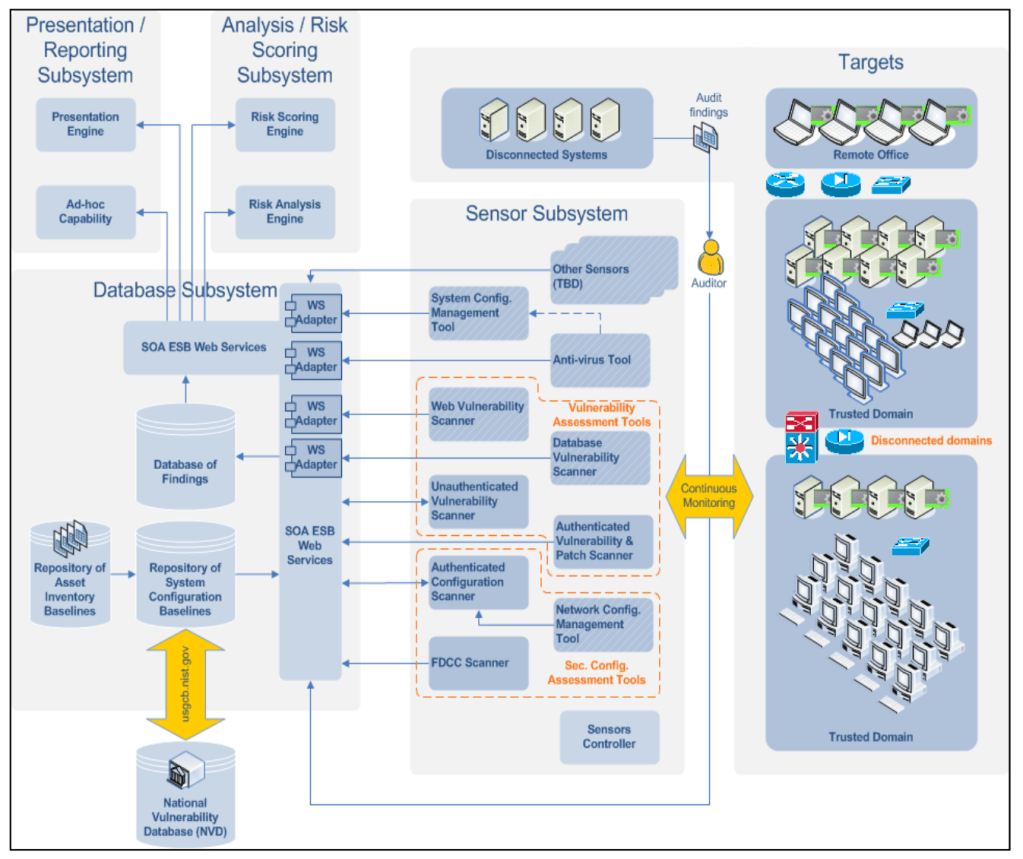
Knowing your existing assets, threats and countermeasures is a necessary step in establishing a starting point to begin prioritising cyber risk management activities. Indeed, when driving the improvement of the security posture in an organisation, security leaders often begin with getting a view of the effectiveness of security controls.
A common approach is to perform a security assessment that involves interviewing stakeholders and reviewing policies in line with a security framework (e.g. NIST CSF).
A report is then produced presenting the current state and highlighting the gaps. It can then be used to gain wider leadership support for a remediation programme, justifying the investment for security uplift initiatives. I wrote a number of these reports myself while working as a consultant and also internally in the first few weeks of being a CISO.
These reports have a lot of merits but they also have limitations. They are, by definition, point-in-time: the document is out of date the day after it’s produced, or even sooner. The threat landscape has already shifted, state of assets and controls changed and business context and priorities are no longer the same.

I have been fortunate to help and collaborate with a wide variety of organisations during my cyber security career to date. These companies range from large multinationals that are household names to small tech startups that you probably haven’t even heard of.
Although the regulatory landscape, security maturity and key risks often vary dramatically between industries, there are common themes that both an upstart FinTech and an energy giant can benefit from.
Being able to see what works, for example, in the world of Operational Technology and apply some of the learnings to an insurance company and vice versa can bring a fresh perspective and result in unique solutions that can be easily overlooked in traditional sector-specific paradigms. Identifying these synergies and collaboration opportunities between organisations of different sizes, industries, cultures and technological stacks has allowed me to better understand specific issues, challenge the conventional thinking and tailor my advice to fit the overall strategy of a given organisation for best results.

I recently passed the AZ-500: Microsoft Azure Security Technologies exam and earned the
Microsoft Certified: Azure Security Engineer Associate credential. In this blog I would like to share some tips that will help you prepare and ace it too.
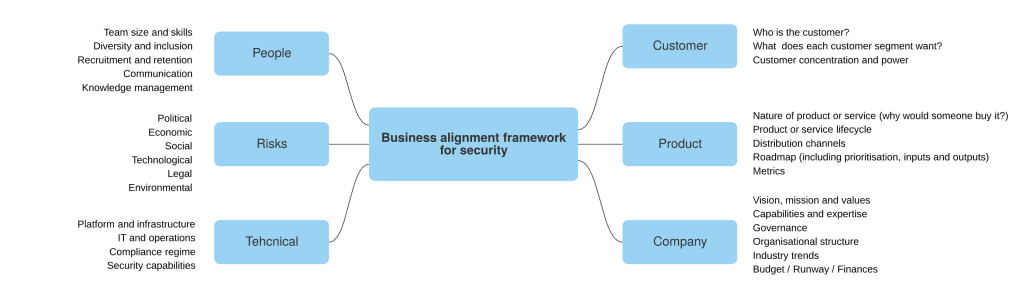
In my previous blogs on the role of the CISO, CISO’s first 100 days and developing security strategy and architecture, I described some of the points a security leader should consider initially while formulating an approach to supporting an organisation. I wanted to build on this and summarise some of the business parameters in a high-level framework that can be used as a guide to learn about the company in order to tailor a security strategy accordingly.
This framework can also be used as a due diligence cheat sheet while deciding on or prioritising potential opportunities – feel free to adapt it to your needs.

I’ve been invited to speak at the CSO30 Conference today on applying behavioural science to cyber security.
I talked about the role behavioural science plays in improving cybersecurity in organisations, the challenges of applying academic theory in practice and how to overcome them.
I shared some tips on how to build the culture of security and measure the success of your security programme.
We also spoke about the differences in approaches and scalability of your security programme depending on the size and context you organisation, including staffing and resourcing constraints.
Overall, I think we covered a lot of ground in just 30 minutes and registration is still open if you’d like to watch a recording.