
Cyber security strategy and execution is one of the top priorities for a CISO. It helps articulate the value of security, provide clarity on short and long term goals and outline a cyber security uplift roadmap.
In this blog I recommend a proven step-by-step guide for developing a cyber strategy.
Understanding the context of the organisation is an important first step, particularly if you recently accepted a role in a new organisation. Based on my experience, there are three main aspects in the wider context affecting most businesses:
- Increasing threat. Rise of organised cybercrime and state sponsored attacks sees malicious actors increasing their level of capability and broadening their targeting (e.g. ransomware).
- Regulatory and contractual obligations. Security regulation is evolving, increasing breadth and depth of controls and rising fines. Customers, partners and regulators are increasing focus on security and data protection.
- Digital transformation. Accelerated pace of technology change and adoption (e.g. Cloud, AI) leads to high-impact systemic risks. Furthermore, evolving product strategy and innovation creates new risks and compliance implications.
Security strategy should respond by mitigating threats, meeting obligations and enabling business agility.

The pace of change of technology, threats and regulation means that the security strategy itself needs to be agile. A major component of the strategy development is the focus on culture, security team identity and mission. Values and behaviours is a major component of this.
Creating an overarching mission statement can facilitate greater internal and external alignment. I recommend focusing on business enablement as much as possible. For instance, the security team’s mission could be to “enable secure products that deliver an innovative experience and build customer trust.” I focused on product-led strategy in this example – feel free to adjust it to the needs of your business.
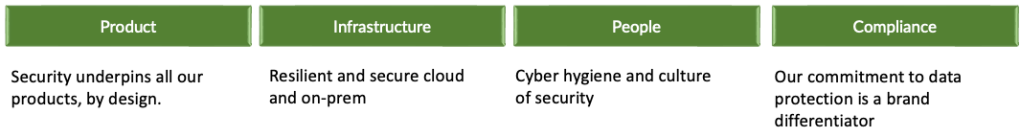
Once you’ve got the buy-in on the security mission from your team and business stakeholders, it’s essential to clearly articulate key areas of focus of your security strategy. For example:
- Product. Security underpins all our products, by design.
- Infrastructure. Resilient and secure cloud and on-prem.
- People. Cyber hygiene and culture of security.
- Compliance. Our commitment to data protection is a brand differentiator.
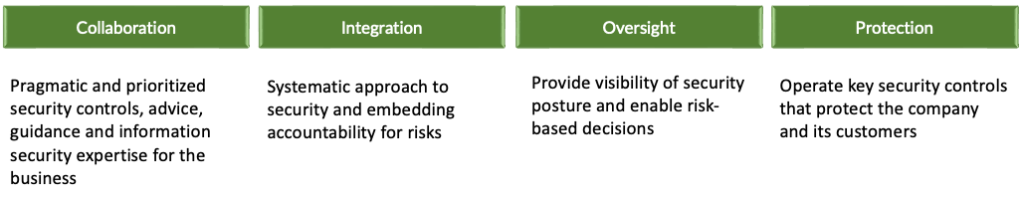
I also recommend developing a set of principles that support the mission and focus areas. For example:
- Collaboration. Pragmatic and prioritised security controls, advice, guidance and information security expertise for the business.
- Integration. Systematic approach to security and embedding accountability for risks.
- Oversight. Provide visibility of security posture and enable risk-based decisions.
- Protection. Operate key security controls that protect the company and its customers.
Cyber security strategy, however, is more than a mission statement and a set of principles. To be effective, it should also include an execution framework that defines and develops security capabilities.
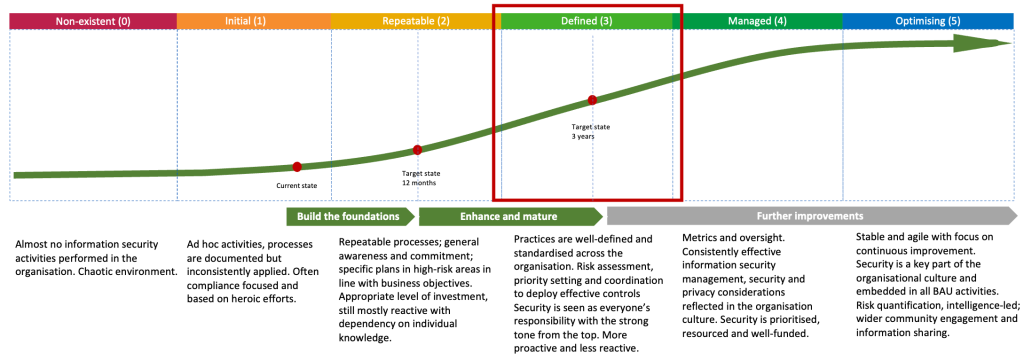
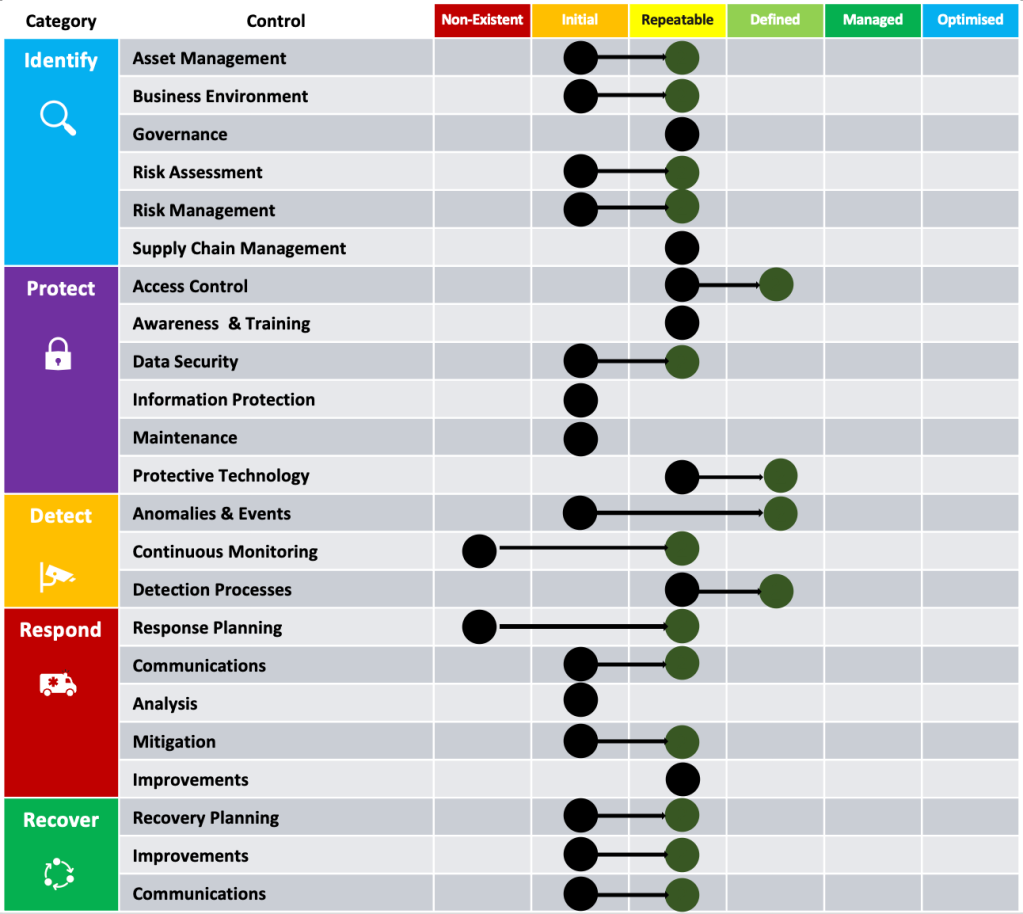
I recommend aligning to a recognised security framework, like the NIST Cybersecurity Framework as it facilitates maturity benchmarking across companies and improves business communication.
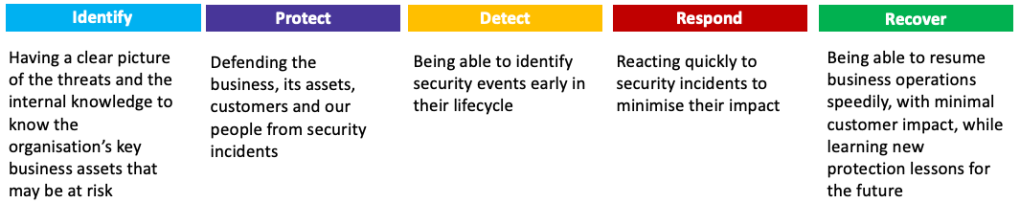
This framework can be used to assess the current state of maturity to define the as-is position. Interviewing stakeholders and reviewing relevant documentation can shed some light on what your baseline is.
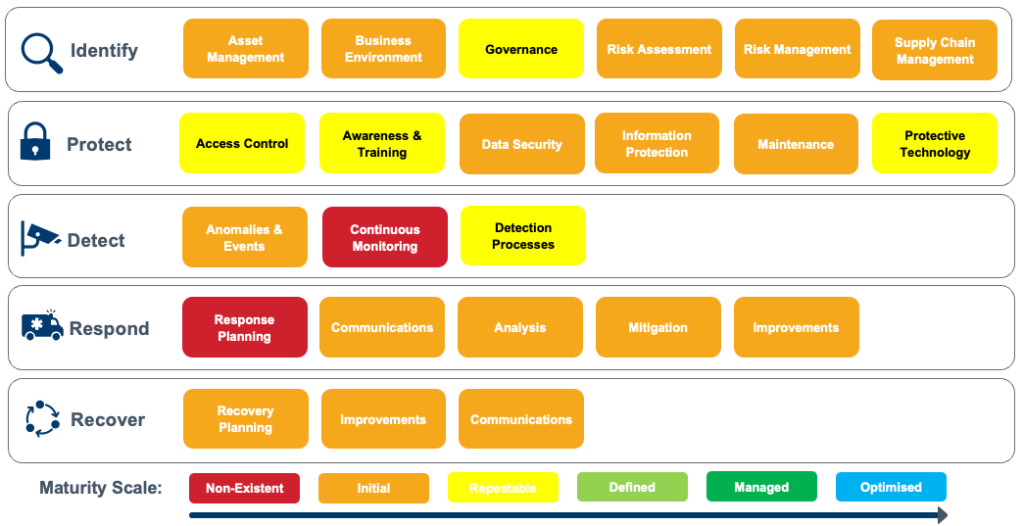
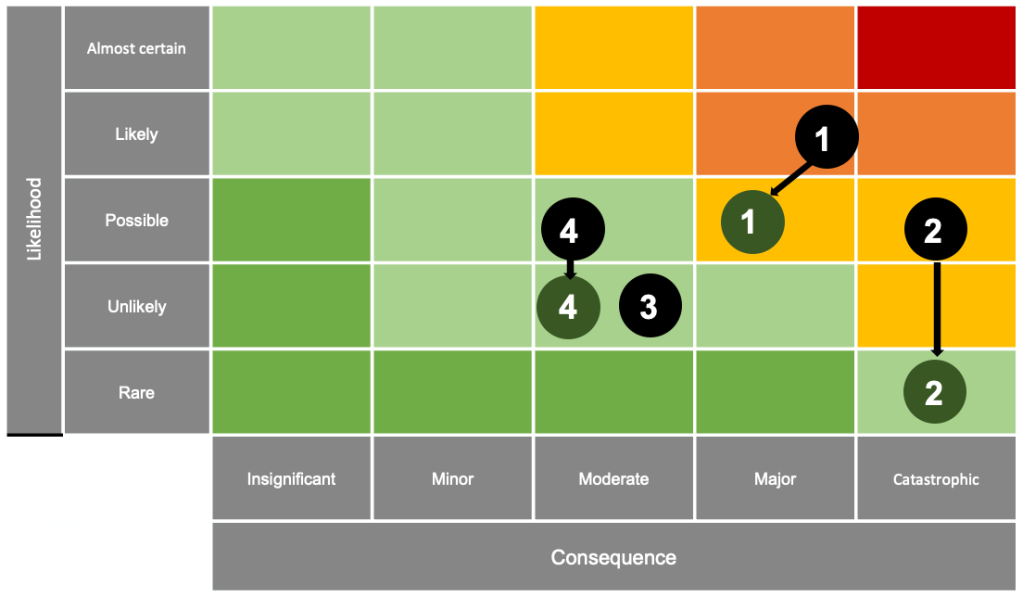
The assessment of key assets, threats and risks is another component to consider. As a result of this exercise, some of the risks (e.g. risk of a data breach) can be reassessed as higher than initially through based on the limited control coverage and capability maturity.
With this in mind, you can then agree with the leadership the desired target capability maturity state might look like for your organisation.
What capabilities should be uplifted to achieve the to-be state? These should translate into specific cyber security initiatives across people, process and technology.
Prioritising these initiatives based on cost-benefit analysis and corresponding risk reduction is the foundation of the cyber security uplift roadmap. It is conditional on appropriate level of funding in tooling, services and people to keep pace with threats and obligations.
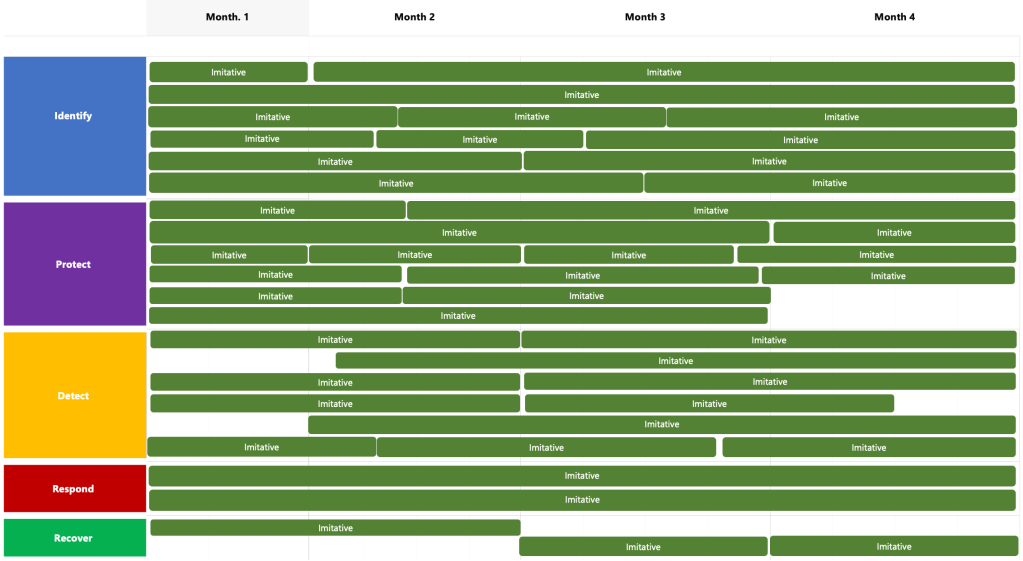
The security strategy should also articulate the indicative risk reduction of the top cyber security risks as a result of executing the proposed capability uplift roadmap. What risks should be managed to bring them within the risk appetite?
You can achieve targeted risk reduction and capability uplift by building the foundations and prioritising right initiatives. The aim is to be reasonable and proportional: absolute security is not possible or even desirable as it won’t be cost-effective. Select and implement your controls and communicate throughout with the leadership.
4 Comments