
I’ve been shortlisted for the CISO of the Year Award! It’s great to be recognised for excellence and innovation in cybersecurity alongside such accomplished leaders in the industry.
A practical approach

I’ve been shortlisted for the CISO of the Year Award! It’s great to be recognised for excellence and innovation in cybersecurity alongside such accomplished leaders in the industry.
To remain competitive, modern technology businesses should take steps to implement responsible business practices that customers, employees and partners expect.
Customers want to purchase products that protect the environment and improve local communities. A useful tool to pursue inclusive growth is a sustainability balanced scorecard.
Below is an example sustainability strategy map I developed for a technology startup.
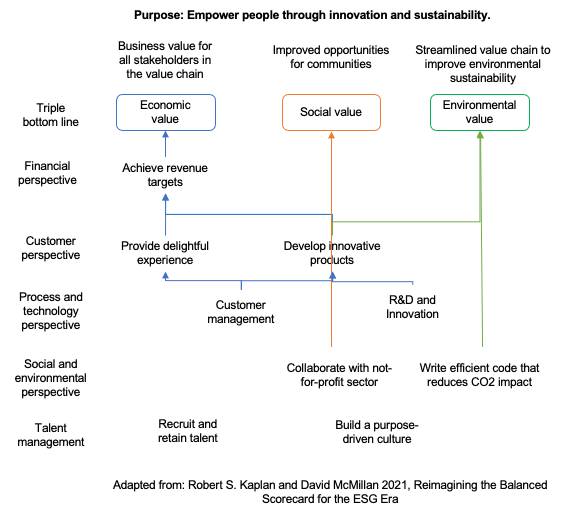
For a technology business, environmental impact can be achieved through close examination and streamlining of company’s supply chain, including datacentres and cloud infrastructure providers. Companies could also analyse their software development lifecycles to make it more sustainable.
Achieving financial objectives can produce societal benefits through creating shared value.
Finally, implementing responsible business practices aligns with UN Sustainable Development Goals (SDGs), specifically SDG9: Industry, Innovation and Infrastructure and SDG17: Partnerships for the Goals.

In this 15 minute interview I spoke with Ed Kennedy of CSO Australia, reflecting on Australian cyber security incidents of 2022, leadership and my approach and insights to cyber security at Linkly.
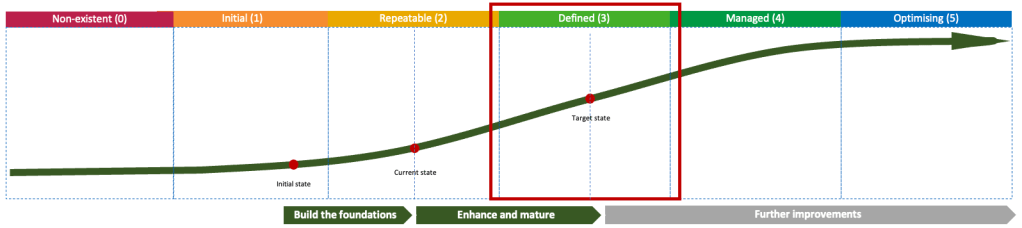
CISOs and security leaders are often called upon to develop a security strategy. It’s an important step to understand what your current state is, in what direction you’re going and the roadmap to get there. It’s also an opportunity to demonstrate how cyber security activities and programs align to business objectives.
There is more to the CISO role than just setting the direction, however. It’s also about execution. As a security leader, it’s key to take ownership of the strategy and deliver on its promise. It’s useful, therefore, to be able to track progress against your objectives and demonstrate to the executive leadership team and the Board the impact the security team is making in enabling the business.

I had a great day speaking at the Cloud Security Summit on ransomware threats in cloud environments and how they’ve evolved over time. In this discussion I shared tips on the essential elements of a robust ransomware defence strategy in the Cloud and specific steps for incident response planning and recovery strategies.
I also provided recommendations for aligning cloud security measures with an organisation’s existing IT architecture and strategy, and how can businesses ensure this alignment contributes to their overall security posture effectively. Looking towards the future, I also shared my thoughts on evolutions in ransomware threats, and how can organisations prepare themselves for these events.

Designing a target operating model for an organisation is a complex activity. It is important, therefore, to keep it simple initially. At a very high, level, I suggest CISOs start with three key capabilities:
These can then be decomposed further, tailoring to the needs of your particular organisation. Understand how each domain interacts with and supports the others, capturing key outcomes and dependencies for each function.
Key security capabilities are supported by Leadership and Governance streams, including Security Strategy, Business Alignment, Integration, Oversight, Optimization, Finance, Security Culture, Program Management, Stakeholder Management and Reporting.
Business as usual activities required to keep the lights on are often neglected when capability uplift is prioritized. For this reason, I placed it in the centre of the diagram, emphasising the ongoing importance of providing consistent security service to your organisation.
The NIST Cybersecurity Framework functions at the intersections of domains aim to illustrate the collaborative nature of the security teams. It’s important to go beyond silos , ensuring frequent interaction with the business as well as within the security department.

I had a pleasure to participate in the keynote panel discussion on cyber security Board reporting at the CISO Executive Network event in Sydney. It was an insightful discussion where I had a chance to share my views on aligning on Board expectations, developing relationships and tailoring your message for maximum impact.
We also covered common challenges and strategies for winning the Board over as well as good practices for reporting. It was a great opportunity to contribute to the community and learn from my peers in the industry.

I’m happy to share that after a long review process, our paper on identifying and extracting scam stages and scripts is finally published.
It’s been a great collaboration with Macquarie University to analyse scammers’ strategies that built a foundation for developing a Conversational AI bot that wastes scammers’ time.
Read full paper here: https://arxiv.org/abs/2307.01965

Cyber security strategy and execution is one of the top priorities for a CISO. It helps articulate the value of security, provide clarity on short and long term goals and outline a cyber security uplift roadmap.
In this blog I recommend a proven step-by-step guide for developing a cyber strategy.
Data breaches are unforeseen events that can have significant repercussions for organisations, demanding immediate action, composure, and transparent communication. In this blog, I explore the essential components of managing a data breach and provide practical guidance for security leaders to effectively navigate this complex situation.